Discover our industry leading expertise
Industry Insights
The Silver Lining for your Cloud Migration
No matter where you are on your cloud journey, building an optimal security environment and meeting compliance goals are primary obligations...
Once your UDO is approved for sharing, security still needs to be put into place to enable it for users. ALLOut's enhanced SuperGrid provides easy maintainence of the F00950W table.


UDOs are personalized web-based objects that can be created by users to improve their JDE experience and reduce the requirement for the developer involvement. Below are a couple of examples of a custom UDOs. Whether you need something simple or you need to put several sets of information at your fingertips, E1 UDO functionality can empower you.
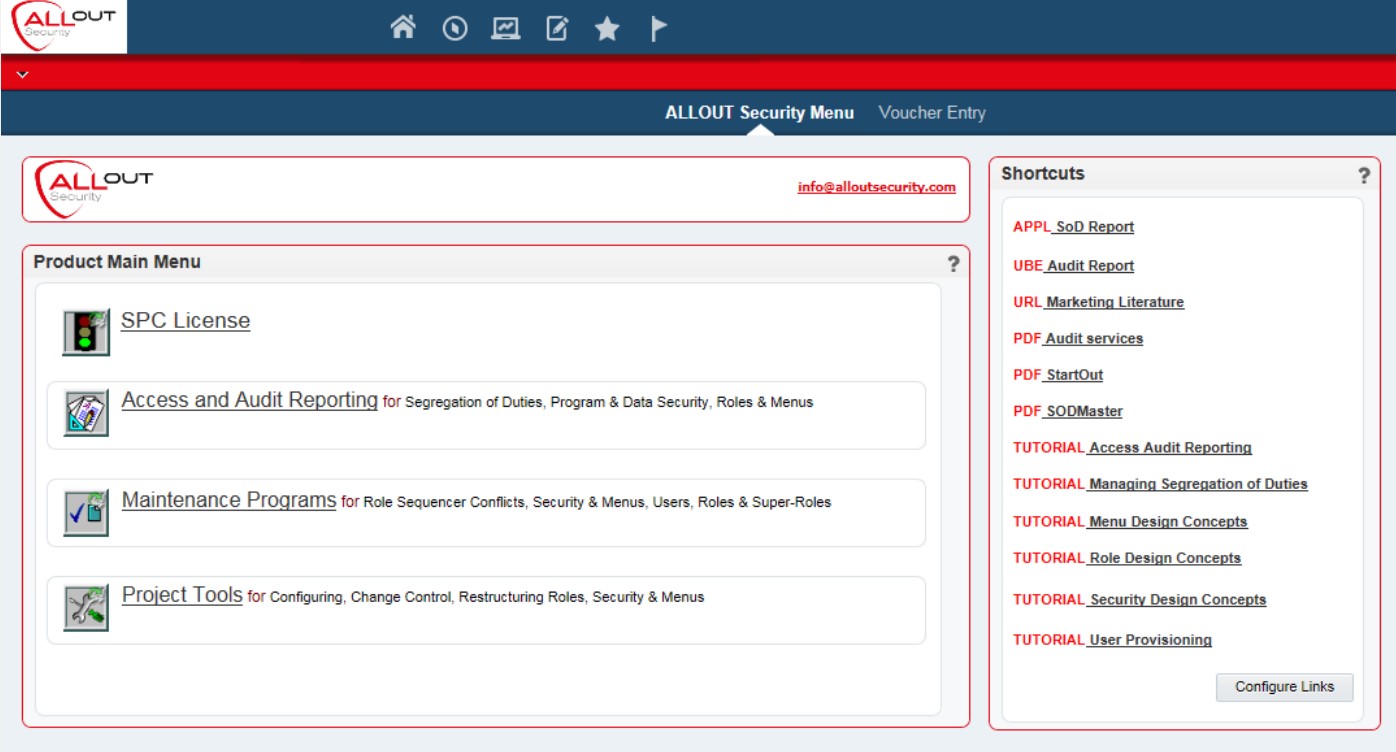
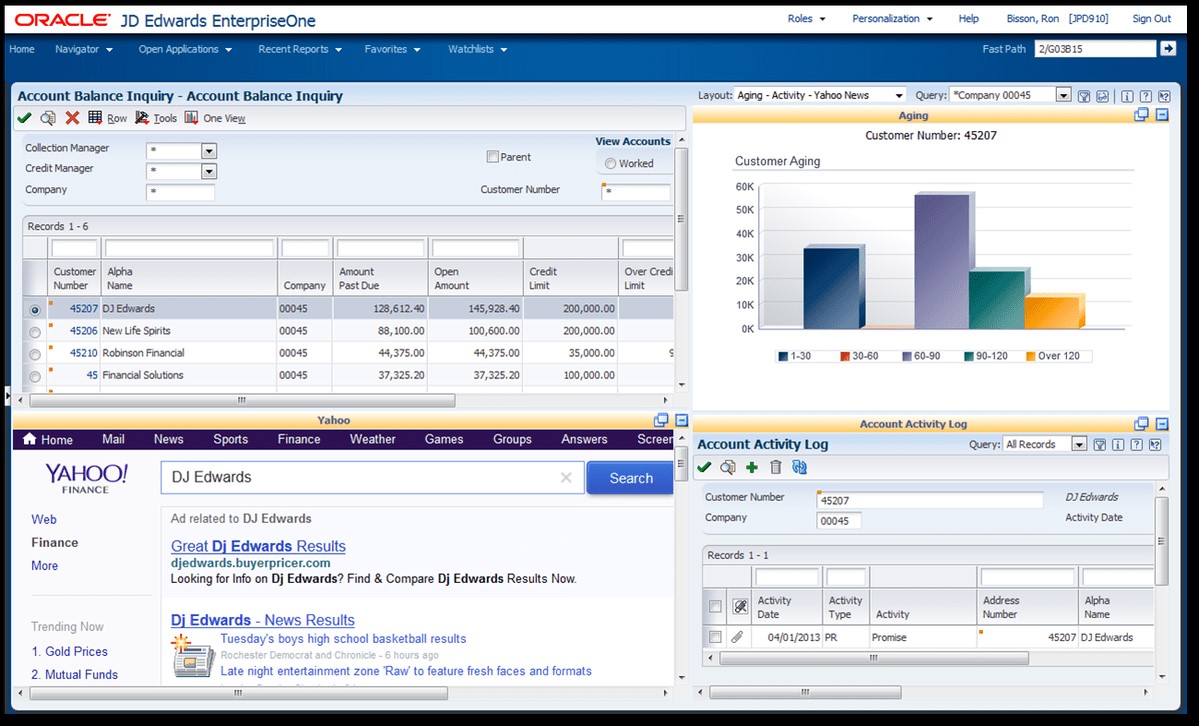
There are various schools of thoughts around who is empowered to do the development of these tools. In reality, the best practice varies by company and the tool. Some, such as queries, may make sense to make available for more users while other, such as the pages above, may make more sense to centralize development on. Either way, once you have your UDO created, now you are ready to share it.
Assuming that the correct authorities exist, a user(s) can develop their own User Defined Objects via the relevant JDE interface – EnterpriseOne contains a design panel (located on the top-right corner of the screen) that provides a coherent way to create and request to publish UDOs. Below is a graphical representation of the steps involved in the User Defined Object lifecycle:
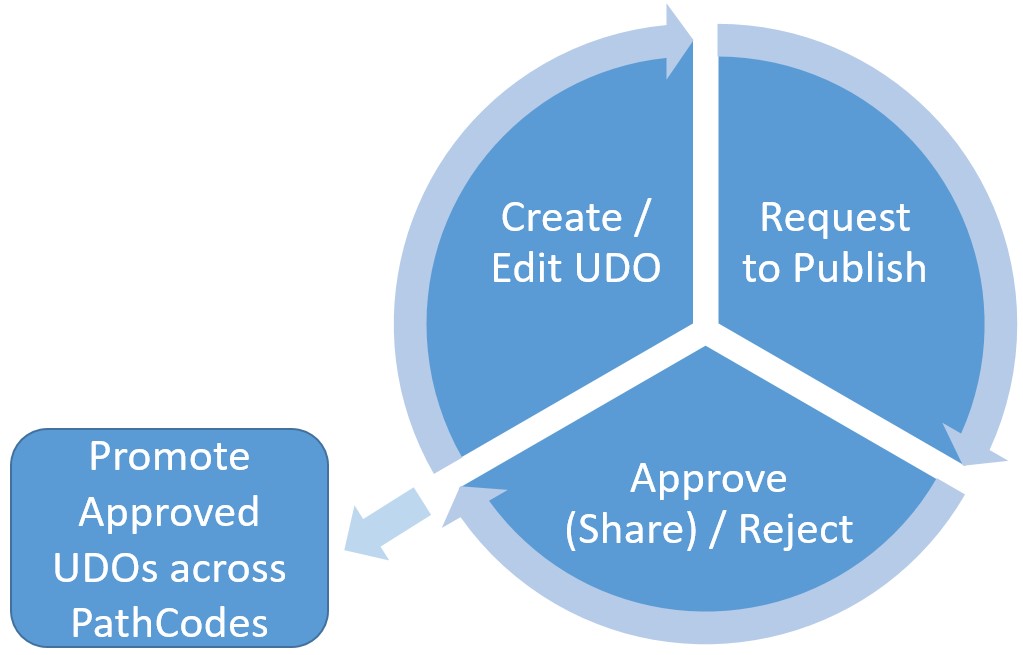
Once the UDO is approved for sharing, security still needs to be put into place to enable it for users. JDE provides security functionality to allow User Defined Objects to be controlled – this security layer (F00950W) sits on top of the standard application security layer (F00950). The full process including the security functionality involved includes:
It is important to develop a strategy around who is responsible for all levels of UDOs security. This can be a complicated process, especially with the multiple layers of security and publishing involved.
As with so many of our tools, ALLOut has identified opportunity to make this process simpler with better visibility to the involved information regarding what is available to the various users and roles. The enhanced ‘Security Maintenance’ SuperGrid (PAOS0950) provides easy-to-use functionality to maintain the F00950W table. The program allows maintenance of all security types (including UDO security) within E1 but with features to speed up your maintenance.
To access the SuperGrid from the ‘Security’ tab of the ‘Maintenance’ screen (PAOS0001), click Maintain Security in ‘SuperGrid’’ or FastPath to PAOS0950.
The above screenshot shows all available UDO ‘Features’ that have been enabled – select the form exit Feature Security to change the available mode.
For more information on UDOs and how to secure them, email hazel.jackson@alloutsecurity.com for a Tutorial and Product Brief or to find out how to view one of our recorded webinars.
A sustainable security and compliance model depends on visibility and confidence. For Prinova, that meant moving from reactive security management to taking control directly within JD Edwards.
Register NowJD Edwards customers can transform their GRC strategy while leveraging AI, but success depends on having best practice security data as the foundation.
Register NowSave time, enhance risk visibility and be audit-ready with ALLOut Security for JD Edwards.
We use cookies to give you the best online experience. By agreeing you accept the use of cookies in accordance with our cookie policy. You can always revoke your consent by clicking on the icon at the bottom left of the screen.

When you visit any web site, it may store or retrieve information on your browser, mostly in the form of cookies. Control your personal Cookie Services here.
| Cookie name | Default expiration time | Description |
|---|---|---|
| _ga | 2 years | Used to distinguish users. |
| _gid | 24 hours | Used to distinguish users. |
| _ga_<container-id> | 2 years | Used to persist session state. |
| _gac_gb_<container-id> | 90 days | Contains campaign related information. If you have linked your Google Analytics and Google Ads accounts, Google Ads website conversion tags will read this cookie unless you opt-out. Learn more. |
| visitor_id<accountid> | The visitor cookie includes a unique visitor ID and the unique identifier for your account. For example, the cookie name visitor_id12345 stores the visitor ID 1010101010. The account identifier, 12345, makes sure that the visitor is tracked on the correct Pardot account. The visitor value is the visitor_id in your Pardot account. This cookie is set for visitors by the Pardot tracking code. |
| pi_opt_in<accountid> | If Tracking Opt-in preferences is enabled, the pi_opt_in cookie is set with a true or false value when the visitor opts in or out of tracking. If a visitor opts in, the value is set to true, and the visitor is cookied and tracked. If the visitor opts out or ignores the opt-in banner, the opt-in cookie value is set to false. The visitor cookie is disabled, and the visitor is not tracked. |
| visitor_id<accountid>-hash | The visitor hash cookie contains the account ID and stores a unique hash. For example, the cookie name visitor_id12345-hash stores the hash “855c3697d9979e78ac404c4ba2c66533”, and the account ID is 12345. This cookie is a security measure to make sure that a malicious user can’t fake a visitor from Pardot and access corresponding prospect information. |
| lpv<accountid> | This LPV cookie is set to keep Pardot from tracking multiple page views on a single asset over a 30-minute session. For example, if a visitor reloads a landing page several times over a 30-minute period, this cookie keeps each reload from being tracked as a page view. |
| pardot | A session cookie named pardot is set in your browser while you’re logged in to Pardot as a user or when a visitor accesses a form, landing page, or page with Pardot tracking code. The cookie denotes an active session and isn’t used for tracking. |
| Cookie name | Default expiration time | Description |
|---|---|---|
| _ga | 2 years | Used to distinguish users. |
| _gid | 24 hours | Used to distinguish users. |
| _ga_<container-id> | 2 years | Used to persist session state. |
| _gac_gb_<container-id> | 90 days | Contains campaign related information. If you have linked your Google Analytics and Google Ads accounts, Google Ads website conversion tags will read this cookie unless you opt-out. Learn more. |
| visitor_id<accountid> | The visitor cookie includes a unique visitor ID and the unique identifier for your account. For example, the cookie name visitor_id12345 stores the visitor ID 1010101010. The account identifier, 12345, makes sure that the visitor is tracked on the correct Pardot account. The visitor value is the visitor_id in your Pardot account. This cookie is set for visitors by the Pardot tracking code. |
| pi_opt_in<accountid> | If Tracking Opt-in preferences is enabled, the pi_opt_in cookie is set with a true or false value when the visitor opts in or out of tracking. If a visitor opts in, the value is set to true, and the visitor is cookied and tracked. If the visitor opts out or ignores the opt-in banner, the opt-in cookie value is set to false. The visitor cookie is disabled, and the visitor is not tracked. |
| visitor_id<accountid>-hash | The visitor hash cookie contains the account ID and stores a unique hash. For example, the cookie name visitor_id12345-hash stores the hash “855c3697d9979e78ac404c4ba2c66533”, and the account ID is 12345. This cookie is a security measure to make sure that a malicious user can’t fake a visitor from Pardot and access corresponding prospect information. |
| lpv<accountid> | This LPV cookie is set to keep Pardot from tracking multiple page views on a single asset over a 30-minute session. For example, if a visitor reloads a landing page several times over a 30-minute period, this cookie keeps each reload from being tracked as a page view. |
| pardot | A session cookie named pardot is set in your browser while you’re logged in to Pardot as a user or when a visitor accesses a form, landing page, or page with Pardot tracking code. The cookie denotes an active session and isn’t used for tracking. |